Today’s Business Reliance on Electronic Data and the Expanding Threat
Most, if not all data that businesses utilize throughout day-to-day operations is created, processed, and stored in electronic form. Technology has completely transformed the way companies conduct business and has introduced numerous benefits, including cost savings and increased productivity. Despite the many benefits technology introduces, the use of this technology in day-to-day operations also present significant risks, both from a regulatory and an ethical perspective.
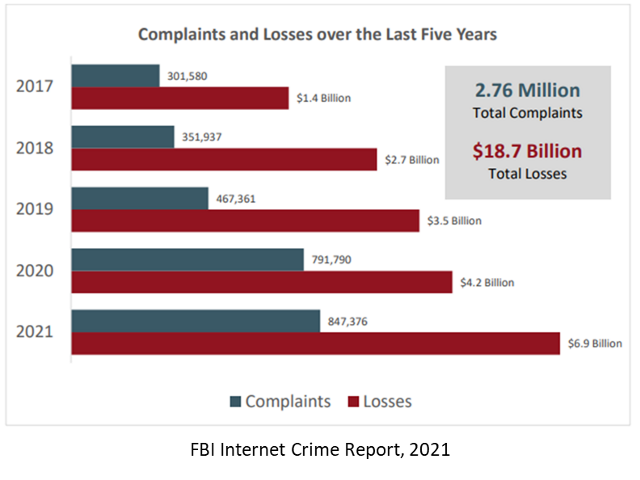
The creation, usage, communication, and storage of data in electronic form introduces the risk of unauthorized access, use, disclosure, alteration, loss, or destruction of the information being stored. We all hear stories in the news of corporations of various sizes and industries falling victim to cybercrime. Today, cybercriminals are looking for every opportunity to indiscriminately attack any business that is unprepared. Therefore, its essential that all businesses implement appropriate security measures to protect their data and their customers’ data.
Regardless of industry, every business must weigh the risks of cyber-incident against the cost of preventing a potential attack. We also know that the threat landscape increases dramatically every year as bad actors design and share more creative ways of attacking systems and the data these systems hold.
Protecting your systems and your data are sound business practices that impact your effectiveness, productivity, and reputation. Furthermore, many businesses are subject to statutory or regulatory requirements with which they must comply.
In the United States, a whole suite of new regulations and laws are being introduced. The Federal Trade Commission, Food and Drug Administration, Department of Transportation, Department of Energy, and Cybersecurity and Infrastructure Security Agency are all working on new rules and regulations related to the way businesses should leverage technology. In addition, in 2021 alone, 36 states enacted new cybersecurity legislation. Globally, there are many initiatives such as China and Russia’s data localization requirements, India’s CERT-In incident reporting requirements, and the EU’s GDPR and its incident reporting.
In the United States, for instance, the White House, Congress, the Securities and Exchange Commission (SEC), and many other agencies and local governments are considering, pursuing, or starting to enforce new rules and regulations. Companies need not site idle waiting for these rules to be finalized and then enforced. They should and can act now to understand the intent of these regulations and take action. Most of these laws and regulations share common elements and represent common sense best practices that should be followed to protect your business regardless of external regulations.
All these laws and regulations share a common focus on the reasonableness or appropriateness of security. Information security is not a “one size fits all approach” and varies depending on the sensitivity of the data companies utilize, the amount of data they utilize, and types of data they utilize. Companies should develop a process driven approach, meaning that information security is a process, not a product. Legal compliance with security obligations involves applying a process to achieve certain objectives, rather than implementing a check list of security measures in all cases.
Ethical Obligations to Safeguard Information
When it comes to an lawyer’s ethical obligations to protect clients’ data, ABA Formal Ethics Opinion 477R operates as the seminal guidance on a lawyer’s ethical obligation to maintain the security of client confidential information in today’s digital landscape.
This opinion reviews aspects that should be considered by, and guide lawyers in making a “reasonable efforts” analysis. In many ways, this opinion distills the ethics guidance of the last 20 years and updates it in light of the current technology environment.
Ethical guidance is also reflected in amendments to Rule 1.1 “Competence” and Rule 1.6 “Confidentiality of Information,” in the ABA Model Rules of Professional Conduct, which were updated to reflect a lawyer’s obligation to protect client confidences when transmitting information over the internet.
Many firms struggle with turning these high-level requirements into actions to address their ethical obligations while balancing the risk with the associated costs of avoiding these threats. Working with a trusted Managed Security Service Provider (MSSP), can help your firm stay abreast of the evolving guidance and expanding threat landscape.
Now that we’ve explored the issues facing today’s firms and understand the ABA’s high-level opinion regarding safeguarding information, our next blog post will outline the top 10 practical considerations to safeguard information. Look for part II in this series, “Lawyer’s Practical Considerations to Safeguard Information”.
Post provided by Vivitec.
![]()


